How to Build a VM Program from Scratch for Your Small Business
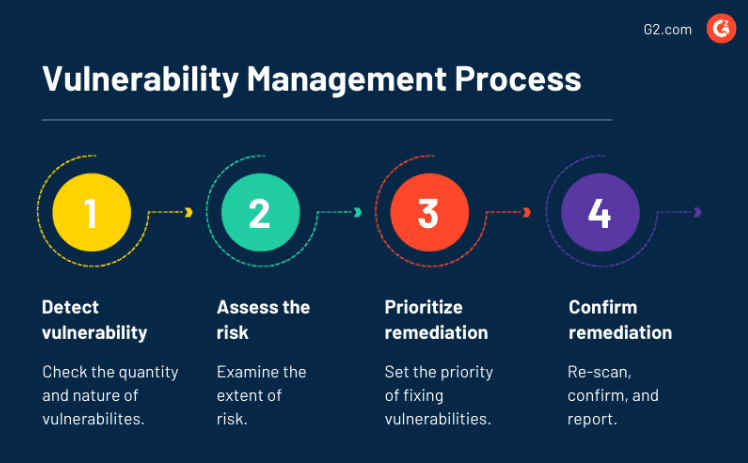
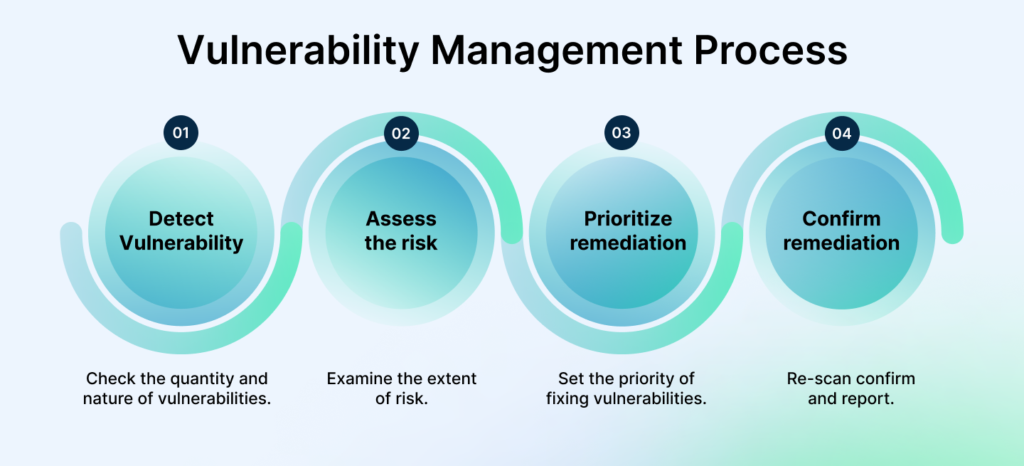
In today’s digital landscape, small businesses must prioritize cybersecurity to protect sensitive data and maintain customer trust. A Vulnerability Management (VM) program is a proactive approach to identifying, assessing, and mitigating security weaknesses in your IT infrastructure. Building a VM program from scratch may seem daunting, but with a structured plan, even small businesses with limited resources can establish an effective system. This article outlines a step-by-step guide to creating a VM program tailored to your small business needs.
Why Your Small Business Needs a VM Program
Cyberattacks, such as ransomware and data breaches, are increasingly targeting small businesses due to their often limited security resources. According to a 2023 report by Verizon, 43% of cyberattacks target small businesses, and 60% of those businesses fail within six months of a breach. A VM program helps you:
- Identify vulnerabilities before attackers exploit them.
- Protect customer data and maintain compliance with regulations (e.g., GDPR, CCPA).
- Reduce financial and reputational risks.
- Build trust with customers and partners.
Step 1: Define Goals and Scope
Before diving into technical details, establish clear objectives for your VM program. Ask yourself:
- What are you protecting? Identify critical assets, such as customer databases, financial records, or intellectual property.
- What are your compliance requirements? Determine if regulations like HIPAA or PCI-DSS apply to your business.
- What is your risk tolerance? Decide how much risk your business can accept and prioritize vulnerabilities accordingly.
Scope your program by mapping out your IT environment, including:
- Hardware (servers, workstations, IoT devices).
- Software (applications, operating systems).
- Network infrastructure (routers, firewalls).
- Cloud services (e.g., AWS, Google Workspace).
For small businesses, start with a narrow scope—focus on critical systems—and expand as resources allow.
Step 2: Assemble a VM Team
Even with a small team, designate roles to ensure accountability. Key roles include:
- Program Lead: Oversees the VM program, coordinates tasks, and reports to management (this could be the business owner or IT manager).
- IT Staff or Contractor: Performs scans, patches systems, and implements fixes.
- Stakeholders: Department heads or employees who provide input on critical assets and operational needs.
If your business lacks in-house expertise, consider outsourcing to a managed security service provider (MSSP) for tasks like vulnerability scanning or penetration testing.
Step 3: Conduct an Asset Inventory
A comprehensive asset inventory is the foundation of your VM program. Document all hardware, software, and services in your IT environment. For each asset, record:
- Asset type (e.g., server, application).
- Owner (e.g., IT department, third-party vendor).
- Criticality (e.g., high, medium, low).
- Location (e.g., on-premises, cloud).
Use free or affordable tools like Spiceworks Inventory or Open-AudIT to automate asset discovery for small businesses. Regularly update the inventory to account for new devices or software.
Step 4: Perform Vulnerability Scanning
Vulnerability scanning identifies weaknesses in your systems. Choose a scanning tool that fits your budget and technical expertise. Options include:
- Free Tools: OpenVAS or Nmap for basic scanning.
- Paid Tools: Nessus Essentials (free for up to 16 IPs) or Qualys Community Edition for small-scale use.
- Cloud-Based Solutions: Tenable.io or Rapid7 InsightVM for businesses with cloud infrastructure.
Best Practices for Scanning:
- Schedule regular scans (e.g., monthly or quarterly) to balance thoroughness and resource use.
- Start with non-intrusive scans to avoid disrupting operations.
- Scan both internal and external assets, as threats can originate from within or outside your network.
After each scan, generate a report detailing vulnerabilities, their severity (e.g., critical, high, medium, low), and affected assets.
Step 5: Prioritize and Remediate Vulnerabilities
Not all vulnerabilities require immediate action. Use a risk-based approach to prioritize remediation:
- Assess Severity: Most scanning tools assign a Common Vulnerability Scoring System (CVSS) score (0–10). Focus on vulnerabilities with scores of 7 or higher first.
- Consider Asset Criticality: Prioritize fixes for high-value assets (e.g., a customer database over a test server).
- Evaluate Exploitability: Check if a vulnerability has known exploits in the wild using resources like the National Vulnerability Database (NVD) or Exploit-DB.
Remediation Strategies:
- Patch Management: Apply software updates or security patches promptly. Use tools like WSUS (for Windows) or Ansible for automated patching.
- Configuration Changes: Adjust settings (e.g., disable unused ports or services) to reduce attack surfaces.
- Workarounds: If patching isn’t immediately possible, implement temporary measures, such as firewall rules or network segmentation.
- Retire Obsolete Systems: Replace outdated software or hardware that can’t be patched.
Document all remediation actions, including who performed them and when.
Step 6: Monitor and Maintain the Program
A VM program is not a one-time effort—it requires ongoing maintenance. Key activities include:
- Continuous Monitoring: Use tools like Zabbix or Nagios to monitor network activity and detect anomalies.
- Regular Reporting: Share progress with stakeholders, highlighting vulnerabilities found, fixed, and pending.
- Employee Training: Educate staff on security best practices, such as recognizing phishing emails or using strong passwords.
- Program Review: Annually assess your VM program’s effectiveness and adjust goals, tools, or processes as needed.
Step 7: Leverage Free and Affordable Resources
Small businesses often operate on tight budgets. Fortunately, many free or low-cost resources can support your VM program:
- Frameworks: Adopt guidelines from NIST SP 800-53 or CIS Controls (free versions available).
- Communities: Join forums like Reddit’s r/cybersecurity or SANS Small Business Cybersecurity for advice and peer support.
- Training: Access free courses from Cybrary or SANS Cyber Aces to upskill your team.
Common Pitfalls to Avoid
- Ignoring Low-Severity Vulnerabilities: These can be chained together by attackers to create significant breaches.
- Over-Reliance on Automation: Tools can’t catch everything—manual reviews are essential for context.
- Neglecting Employee Awareness: Human error is a leading cause of breaches. Regular training is critical.
- Failing to Document: Without records, it’s hard to track progress or demonstrate compliance.
Conclusion
Building a vulnerability management program from scratch is a manageable task for small businesses with the right approach. By defining clear goals, leveraging affordable tools, and fostering a security-conscious culture, you can protect your business from cyber threats and build resilience. Start small, focus on critical assets, and scale your program as your business grows. With consistent effort, your VM program will become a cornerstone of your cybersecurity strategy, safeguarding your operations and reputation in an increasingly risky digital world.


