Description of the Issue: In September 2025, more than 40 NPM packages were compromised in a large-scale supply-chain attack. The malware executes during installs, steals secrets, and persists through GitHub workflows. Read more here: StepSecurity: Task: Assume your organization is impacted. Write a short report covering: How you discovered the …
Description: On Tuesday September 9, 2025, Microsoft released patches for several of its products. Analyze the CVEs and let us know which ones are most critical in your environment. [Hint: Go to Microsoft website, export the file and analyze.]. America CyberSquad (ACS)September 2025 1 Comment Bright AduakohSeptember 13, 2025 at …
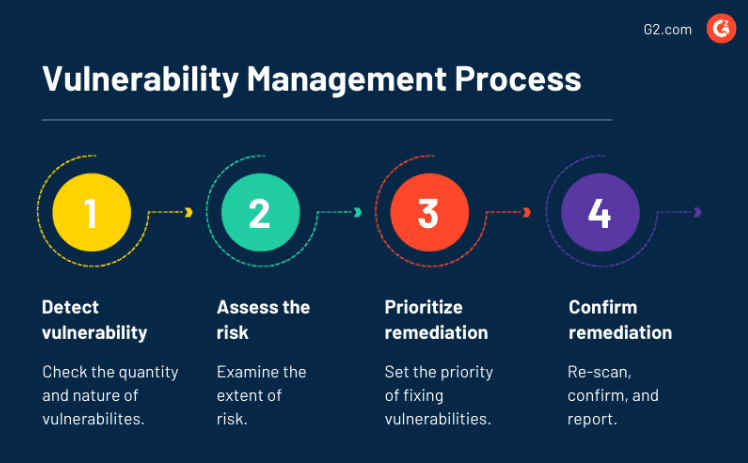
In today’s digital landscape, small businesses must prioritize cybersecurity to protect sensitive data and maintain customer trust. A Vulnerability Management (VM) program is a proactive approach to identifying, assessing, and mitigating security weaknesses in your IT infrastructure. Building a VM program from scratch may seem daunting, but with a structured …
Cloud computing has revolutionized how businesses operate, offering scalability, cost-efficiency, and flexibility. However, the cloud is not a silver bullet for security. Misconfigurations, inadequate access controls, and overlooked vulnerabilities can expose sensitive data to cyberattacks. For small businesses relying on cloud services like AWS, Microsoft Azure, or Google Cloud, understanding …
In today’s digital landscape, small businesses must prioritize cybersecurity to protect sensitive data and maintain customer trust. A Vulnerability Management (VM) program is a proactive approach to identifying, assessing, and mitigating security weaknesses in your IT infrastructure. Building a VM program from scratch may seem daunting, but with a structured …